
Burp-Suite is a very powerful interception proxy that can be used to intercept, manipulate and forward local traffic. Below I would like to shortly introduce its most important features.
Setup
To use https with Burp Suite, it is necessary to set the browser proxy to localhost and start Burp Suite. Afterwards you can open http://burp and download the CA certificate there and integrate it into Firefox: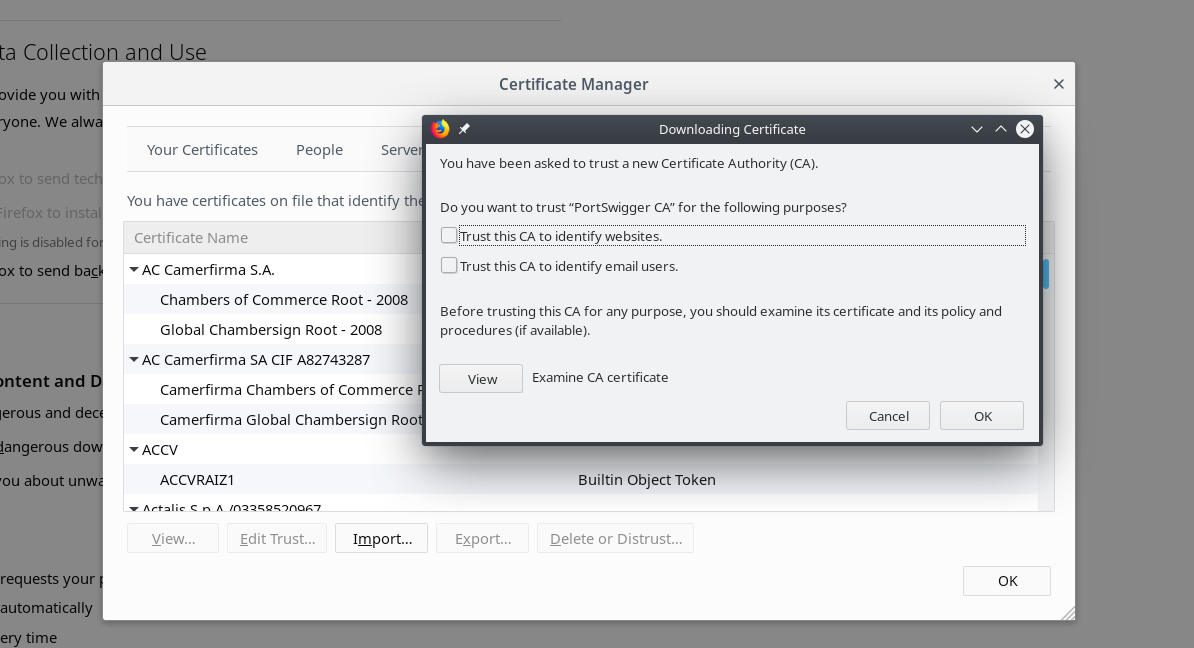
Spider tab
Spider tab is great for finding links and forms on web pages. Spider follows links to a defined depth and can help set the scope of a pentest.
In the Control tab, you can turn the spider on and off, as well as set the scope: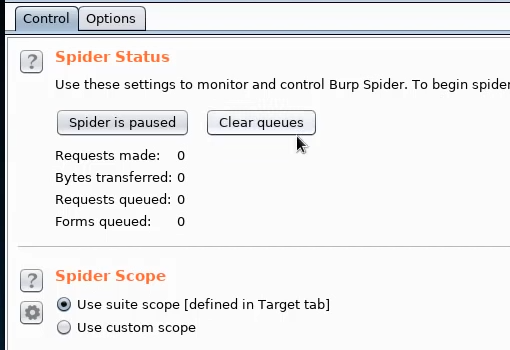
Target tab
You can find all domains and paths that you have visited here.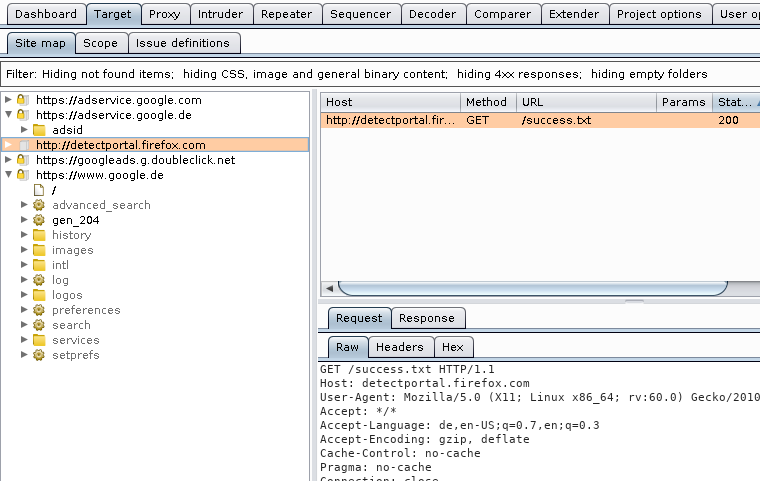
Entries with a gray background mean that those entries are referenced on the web page, but have never been accessed through a request.
The Target tab is mostly used to define the scope of a project: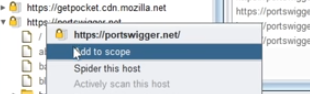
Proxy tab
Here you can specify if traffic should be intercepted and blocked until you forward it. This is done by using the “Intercept” button:
All recorded requests can also be displayed, modified and resent here.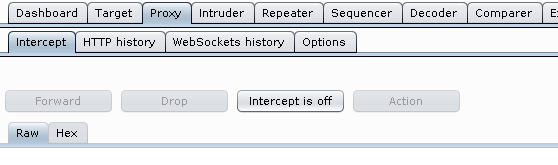
A useful function is “Match and replace”. This can be used, for example, to disable a specific JavaScript code by replacing it with an empty string.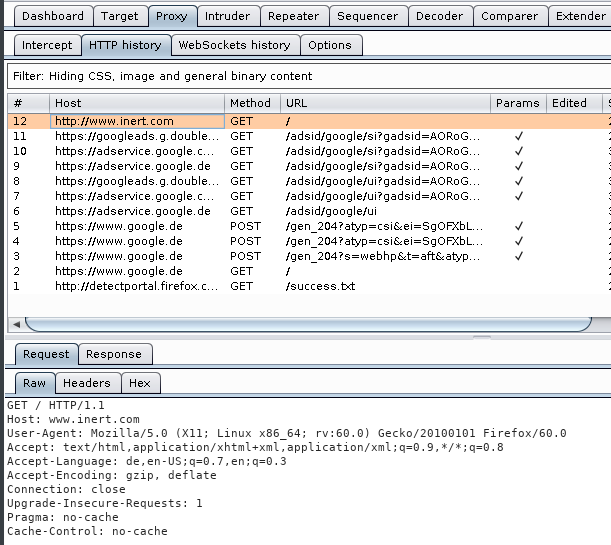
Reponse options are also useful. These can be used, for example, to display and highlight hidden form fields.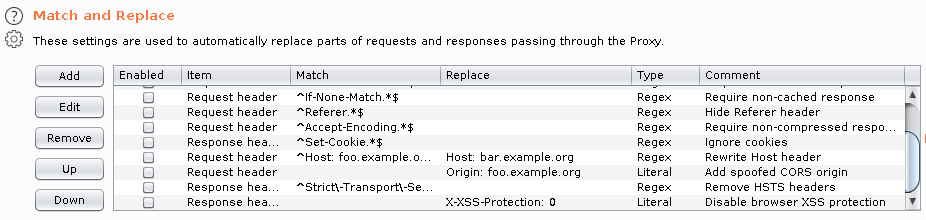
Intruder tab
Data packets can be forwarded towards here in order to modify them, or to use them as templates for automated attacks in large quantities:
Sniper
Benutzt ein set von Payloads und wendet es an den markierten Positionen an.
Battering ram
Das gleiche wie Sniper, aber anstelle alle Payloads seperat zu testen, werden alle Parameter gleichzeitig getestet. Jede Position hat immer den gleichen Wert, den auch die anderen Positionen haben.
Pitchfork
Nimmt ein Payload-Set für jeden parameter und iteriert alle gleichzeitig.
Cluster bomb
Nimmt ein Payload-Set für jeden Parameter und testet alle Varianten unabhänig voneinander durch. Kann eine sehr große Menge an Anfragen generieren und sehr lange dau
Sniper
Uses a set of payloads and applies them to the marked positions.
Battering ram
The same as Sniper, but instead of testing all payloads separately, all parameters are tested simultaneously. Each position always has the same value as the other positions.
Pitchfork
Takes a payload set for each parameter and iterates them all at the same time.
Cluster bomb
Takes a payload set for each parameter and tests through all variants independently. Can generate a very large amount of queries and take a very long time.
Repeater tab
You can send data packets to this location, modify them, send them again and compare the response immediately: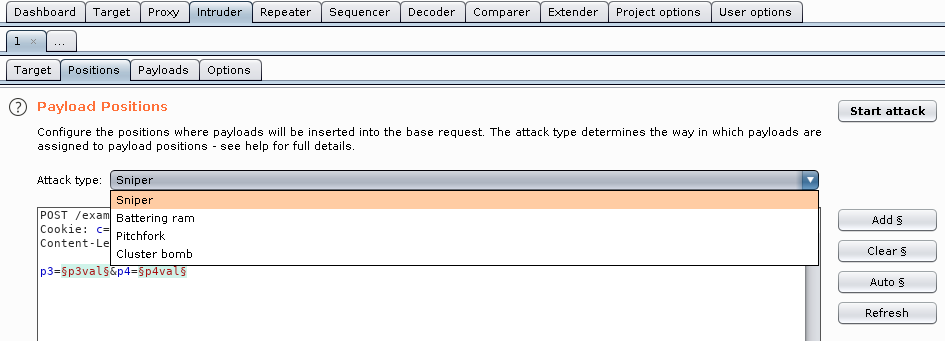
Tip: If you select special characters and press ctrl+u, then they will be encoded.

