A specialty of John the Ripper is that the password algorithms being used are recognized automatically as far as possible and if recognition is not possible, at least helpful suggestions are provided. A disadvantage of John the Ripper is that it uses the CPU and not the GPU to crack the passwords. This means that John the Ripper is many times slower than comparable programs that use the GPU to crack passwords.
John the Ripper can crack hashes in several ways. The most common way is using password lists. Here, all words on a list are tested until one of the words matches the given hash. It is also possible to crack passwords using bruteforce. With bruteforce, all possible character combinations are tried one after the other until there is a match. This method can take a long time, but it is worthwhile especially for randomly generated passwords that do not appear on any password list.
Usage
As soon as John the Ripper is installed, you can use the program with the command “john” within the terminal. To get started, it is recommended, as with most Linux programs, to look at the “man page”. It gives a description of John the Ripper and explains how the program works and of all available parameters. Man pages are documentations of software. The man page of John the Ripper can be accessed by the command “man john”.
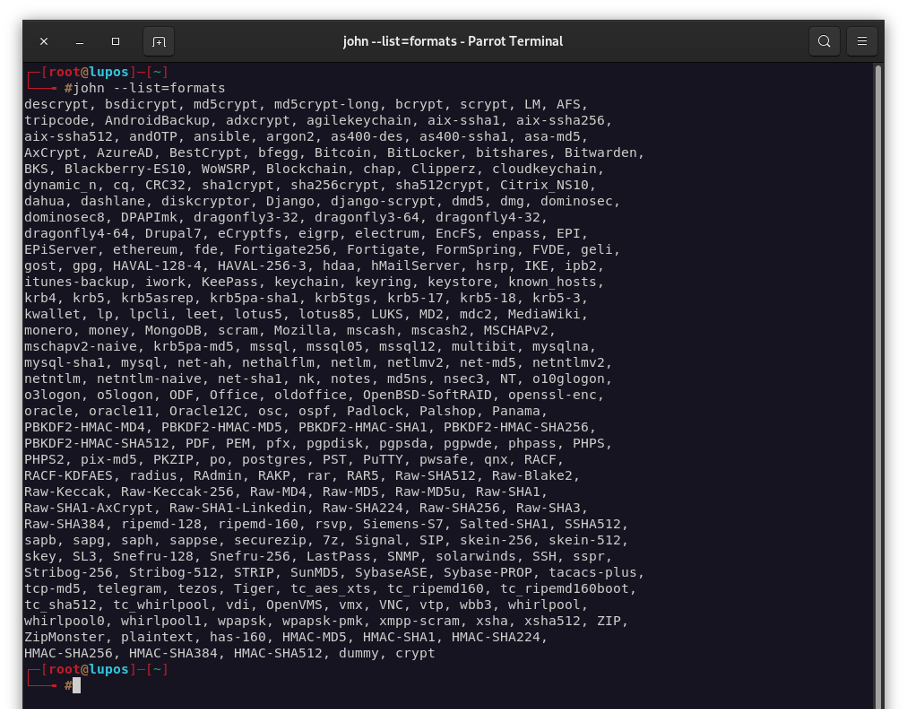
To view all password formats that John the Ripper can deal with, use the command “john –list=formats”:
Generating hashes for testing
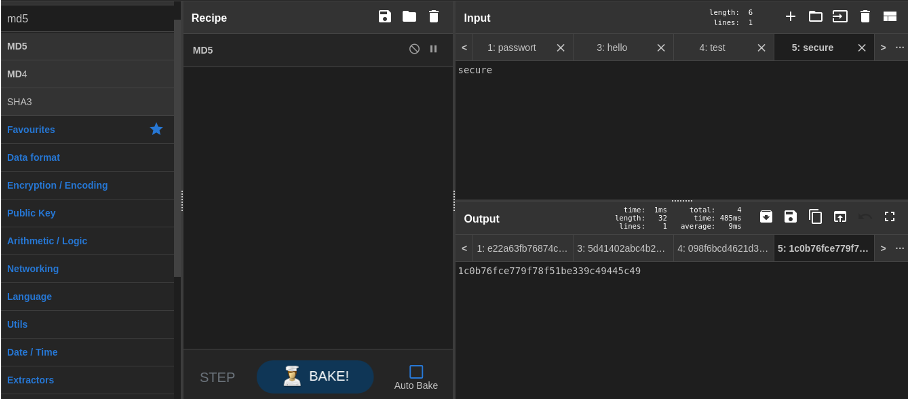
For testing, we generate some hashes of type md5 using the open source tool “CyberChef”, so that we can test John the Ripper:
We now store these hashes with an assignment of dummy usernames in a text file:
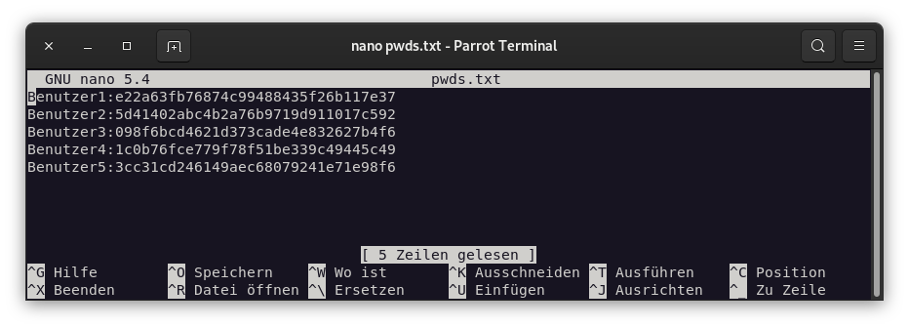
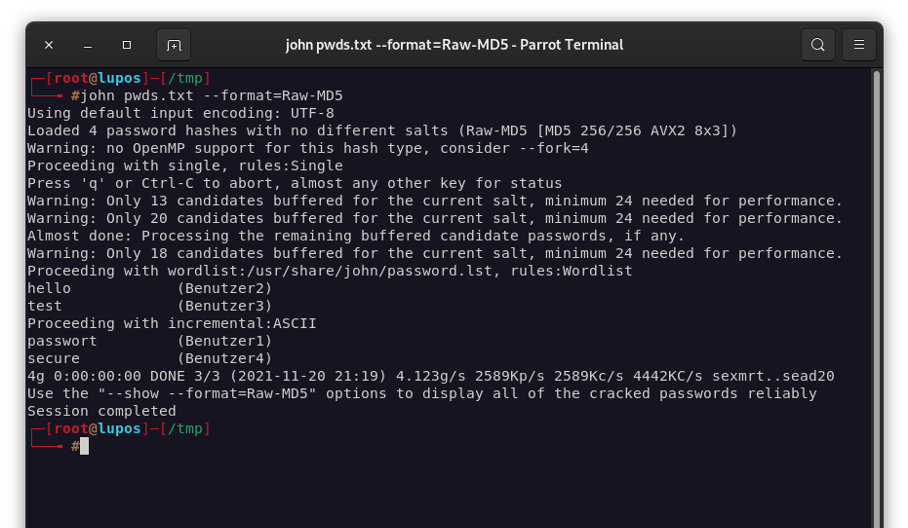
Afterwards we try to crack the hashes with John the Ripper.
Cracking hashes
Within just a few seconds, the hashes were converted back into plain text. John the Ripper also recognized that it is a kind of user - password combination and lists the supposed user names in brackets next to the plaintext.
Now we add a more difficult password (Pa$$w0rd) to the password file to demonstrate the use of word lists. Word lists are collections of different passwords in a text file. Linux distributions such as Kali Linux or ParrotOS already come with a large selection of word lists of various sizes by default. The word lists are usually located in the folder “/usr/share/wordlists”. If the wordlists are missing, you can easily install them with the command “sudo apt install wordlists”. For our example we choose the list “rockyou.txt” as wordlist, because it is already included in Kali-Linux and contains many common passwords:
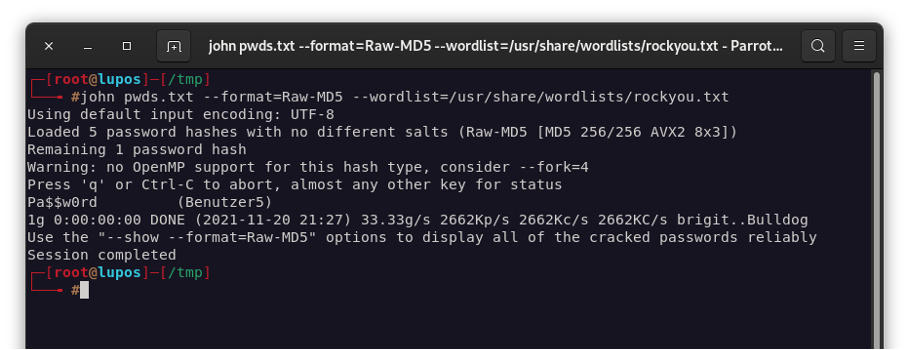
As you can see in the screenshot, the somewhat more difficult password has now also been cracked with ease. John the Ripper didn’t care about the other 4 passwords this time, because they were already cracked and cached before.
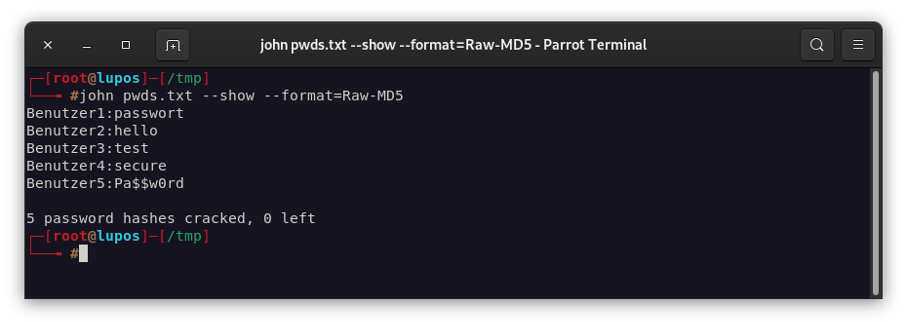
Using the “–show” parameter, all passwords that were cracked in the session can be displayed once again in a structured overview:

Cracking an unknown hash algorithm
If you do not know the algorithm used for a password, John the Ripper can detect it by itself.
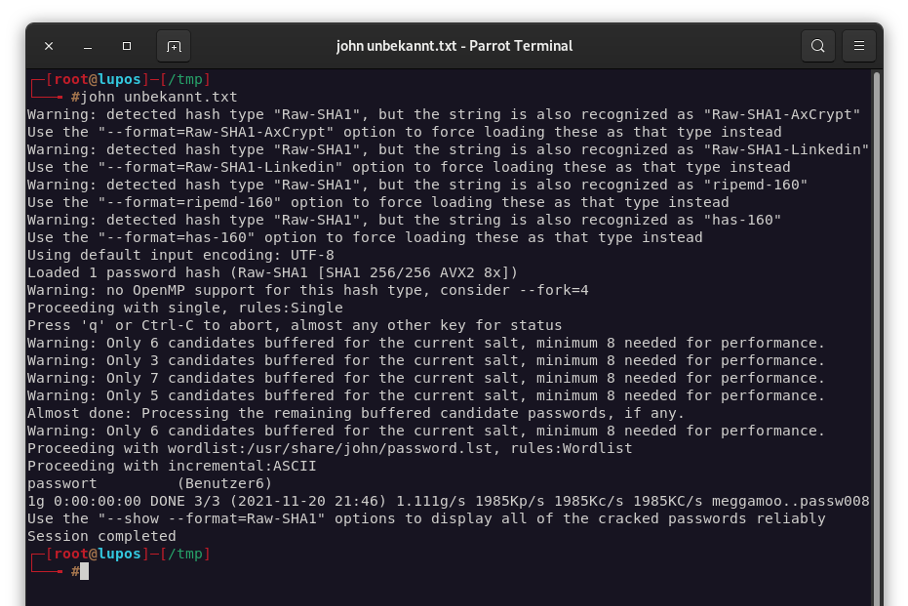
To do this, we create a new text file with a previously generated SHA1 hash and pass this file to John the Ripper without specifying the algorithm we used:
As you can see, John the Ripper easily recognized that it was a SHA1 hash and cracked it properly.
It is also possible to crack Linux passwords with John the Ripper. This is done with the command “john /etc/shadow/”. Depending on the complexity of the password, this can take a very long time.